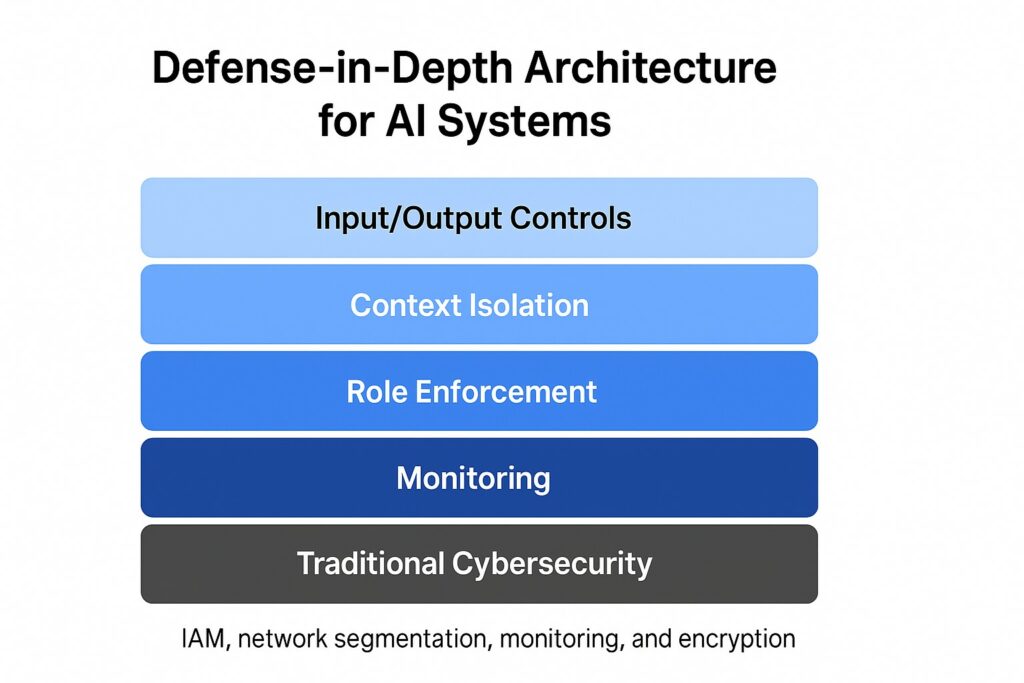
ISO/IEC 62443 – A comprehensive series of standards developed for cybersecurity in Industrial Automation and Control Systems (IACS)
Provides a structured framework that addresses policies, processes, and technical requirements for protecting industrial systems from cyber threats, while ensuring safety, reliability, and resilience. Core Philosophy […]